Canva’s data Breach And The Urgent Call For Cyber Resilience
- Pratichha S.

- Apr 7, 2025
- 7 min read
Updated: Aug 3, 2025

Executive Summary
Risks associated with cybersecurity continue to be a serious issue for every entity, all over the world. In recent years, cyberattacks have increased in frequency, with terrible results for both people and corporations. If you are wondering what is Canva data breach, then this article will explore the breach and the world around it. The Canva data breach, which had an impact on more than 139 million users worldwide, is a stark example of the destruction that a cybersecurity catastrophe may bring about.
Hence, there is a need for businesses to take a proactive approach to cybersecurity risk management. Organisations can take appropriate actions to limit possible risks by recognising and analysing them before they cause a major impact. To protect the safety and security of their data and systems, the research suggests that organisations prioritize risk identification and assessment as part of their cybersecurity strategy.
Introduction
Data breaches are becoming more common in today's digital world, with hackers always looking for new methods to attack flaws in organizations’ cybersecurity defenses. Canva, a well-known online graphic creation tool, is no different. Canva had a data breach in May 2019 that affected the personal information of over 139 million users!
The incident serves as a reminder of the significance of proactively identifying and analysing possible cybersecurity threats, as well as adopting necessary mitigation steps. An important component of every organization’s cybersecurity strategy is risk identification and assessment. It entails a systematic method of detecting possible risks, analysing their possibility and effect, and assessing appropriate risk-mitigation solutions.
The evaluation of this severe data breach is critical because data breaches can have serious repercussions on businesses, including financial loss, legal responsibility, and reputational harm. It is critical to recognize possible risks and put necessary safeguards in place to avoid such accidents. This report will also address any legal compliance issues that may arise concerning Canva's cybersecurity architecture.
What was the Canva Data Breach?
Canva, an Australian graphic design company, had a large data breach in 2019, compromising 139 million user accounts. The attackers obtained email addresses, usernames, names, localities, and encrypted passwords from users. The attack also exposed the encrypted payment card credentials of 78 million users, including card numbers and expiration dates.
Canva, which has over 15 million active users globally, acknowledged the incident and advised users to change their passwords and keep an eye on their financial accounts for unusual behaviour (Antunes et al., 2021). This instance emphasizes the need for good risk identification and assessment in data breach prevention.
Since data breaches can substantially impact a company's finances, legal position, and reputation, this investigation is essential. Financial loss, legal liabilities, and reputational harm could result from a breach. Businesses may reduce the risks of data breaches and perhaps protect both themselves and their customers.
Uncovering Potential Risks in the Canva Data Breach
A cybersecurity professional must detect possible hazards in the client's system and estimate their impact on the organisation. The identification method in the event of the Canva data breach included analysing key vulnerabilities or defects in the client's system, as well as threats made by malevolent adversaries. The identification procedure begins with a thorough examination of the client's system and the data stored on it. The goal is to identify key assets and their susceptibility to cyberattacks. Once important assets have been identified, the next stage is to determine the possible threats to these assets. Natural risks, technological risks, human risks, and legal risks are the four types of hazards.
Initial research indicates that technical difficulties played a major role in the Canva data leak problem. Malicious rivals exploited system weaknesses to gain unlawful access to private data. Inadequate access restrictions, weak passwords, out-of-date software, and a lack of data encryption contributed to the problem. Cybersecurity specialists can assess possible risks using a variety of methodologies, including the Factors Analysis in Information Risk (FAIR), the Privacy Risk Assessment Methodology (PRAM), and the NIST Cybersecurity Framework (CSF) (Sanchez-Iborra & Skarmeta, 2022). These tools assist in the discovery, analysis, and evaluation of risks based on a variety of variables, such as the likelihood that they will occur, possible repercussions, and degree of severity.
Assessing the Canva Data Breach using the FAIR Approach
We can identify and analyse the risks and characteristics using Factor Analysis in Information Risk (FAIR) for the Canva data breach. The usage of the FAIR tool in the Canva data breach scenario aided in identifying the possible dangers related to the incident. The tool assisted in estimating the impact of the breach on the client's system as well as the likelihood of it occurring. It also assessed the financial effect of the breach, such as the cost of data recovery and consumer compensation. This information is presented in the table below in a summarized manner.
Value at Risk (VaR) Formula to Estimate a Firm’s Loss
To understand the loss estimate in a data breach-like issue in a firm, we can estimate it using a manual formula. We multiply the chance of occurrence, potential effect, and duration of each risk to determine the estimated loss. The formula is as follows:
Loss Expected = Probability of Occurrence x Potential Impact x Duration
To visualize the data and emphasize the internal hazards in the Canva Data breach, the following chart can help us a lot:
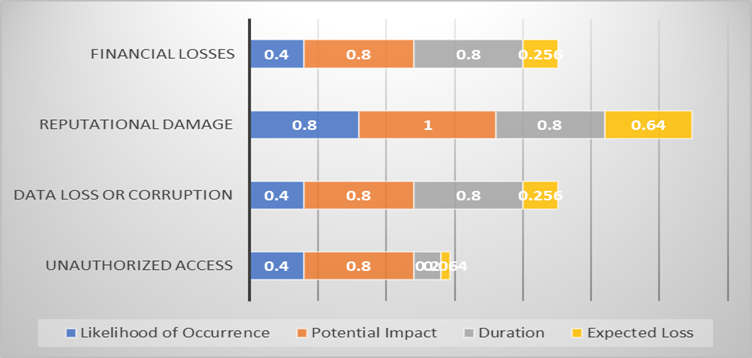
According to the report, the most serious risks are reputational harm and data loss or corruption. To address these risks and prevent a similar incident in the future, it is advised that suitable mitigating measures, such as frequent security audits, data backup and recovery systems, and employee training programs.
Steps to Risk Analysis for Organizations
A Summary of the Analysis Process: Identifying the characteristics of each detected risk and assessing the probable business implications is part of the analytical process. The analytical tool(s) used give a systematic way to evaluate risks and their possible effect.
Identified Risks' Characteristics: The highlighted dangers must be thoroughly examined to establish their characteristics. This comprises the risk's chance of occurrence, the risk's effect, and the vulnerabilities or defects in the system that may lead to the risk. We shall consider both internal and external elements that might contribute to the dangers.
Risk prioritization: The next step is to prioritize the identified risks based on their influence and vulnerability. After all the risks are listed, the organization must prioritize them in an order that aims to resolve the most vulnerable risk first.
Risk Mitigation: After the most vulnerable risk is the first, the final steps are options to mitigate it sequentially. This includes in-depth research, actionable insights, and aligning them with practical steps to reduce the impact of risk.
Recommendation of Appropriate Risk-Mitigation Measures
As per the risks assessed and prioritized, effective strategies to minimize identified risks are proposed. Technical solutions, such as increased security systems, or non-technical solutions, such as personnel training or policy changes, are also included in these measures.
In the instance of Canva's data breach, the firm acted quickly to minimize the situation by changing user passwords and upgrading security procedures. However, the intrusion emphasized the importance of continuing security posture enhancements and frequent risk assessments to identify and mitigate possible threats. Risk evaluation is an important phase in the risk management process since it entails analysing the possible consequences of identified risks and prioritizing them for suitable mitigation actions (Dobrowolski & Sułkowski, 2021). Organisations can successfully manage risks and safeguard their businesses from possible threats by utilizing proven processes and technologies.
To address the identified hazards, organizations and individuals can use a variety of different mitigation techniques. These include:
Employee awareness training: Provide workers with frequent training and awareness programs to ensure they understand their responsibility in securing user data. Educating employees on cybersecurity best practices and how to identify and prevent possible risks through regular employee awareness training programs.
Endpoint protection: It refers to the installation of endpoint protection software on all devices to detect and prevent malware attacks.
Access control rules: These rules are implemented in organizations to decrease the risk of insider threats and unauthorized access to sensitive information.
Third-party risk management: This type of risk management entails creating a complete third-party risk management program to reduce third-party risks.
Authentication and encryption: To secure user data, incorporate extra security measures such as multi-factor authentication and end-to-end encryption.
Review and audits: Conduct frequent audits and reviews of data storage and processing systems to improve data governance practices.
Preventing Data Breaches in Future
The Canva.com data breach emphasizes the need for organisations to take a proactive approach to cybersecurity. Organisations can take efforts to reduce possible threats before they result in a breach by identifying and analysing risks. This strategy not only protects the organisation and its consumers, but it may also improve the organization’s reputation and bottom line.
Cybersecurity threats are evolving in lockstep with technology. As a result, continuous research and development in risk detection and assessment are essential. To handle growing dangers, new approaches and tools may arise, and old frameworks may need to be upgraded. There is also a need for ongoing education and awareness to ensure that organisations are prepared to deal with the ever-changing cybersecurity landscape.
The Canva data leak should act as a wake-up call to businesses of all sizes and sectors. Organisations may take proactive efforts to protect themselves and their customers from possible cyberattacks by prioritizing risk identification and assessment. This article summarizes the identified cybersecurity threats, their possible financial effect, and mitigating options. The firm may strengthen its cybersecurity posture and lower the risk of a possible cyber-attack by following the advice suggested in this study.
Conclusion
The Canva.com data breach is a wake-up call for businesses to prioritize cybersecurity and risk management practices. Companies must have strong risk identification and assessment processes in place in today's digital world when sensitive information is collected and maintained online. Several major discoveries about the Canva data breach event have been made in this research.
First, a weakness in the company's database server was the primary source of the intrusion.
Second, the issue revealed a large quantity of personal information, including email addresses, usernames, and passwords.
Finally, the incident damaged Canva's reputation and credibility among its users.
Organisations must adopt a proactive approach to risk identification and assessment in order to avoid similar disasters in the future. Conducting frequent vulnerability scans, penetration testing, and risk assessments to discover possible threats and weaknesses is part of this. Organisations may then prioritize their cybersecurity efforts and commit resources to the most serious threats first.
Organisations must also employ effective risk mitigation methods to limit their risk exposure. To secure sensitive information from unauthorized access, adopt tight access restrictions, encryption, and network segmentation. Additionally, organisations should give staff regular cybersecurity training and awareness programs to assist them in identifying and reporting possible security breaches.
References
Antunes, M., Maximiano, M., Gomes, R., & Pinto, D. (2021). Information security and cybersecurity management: A case study with SMEs in Portugal. Journal of Cybersecurity and Privacy, 1(2), 219-238. https://doi.org/10.3390/jcp1020012
Dobrowolski, Z., & Sułkowski, Ł. (2021). Business model canvas and energy enterprises. Energies, 14(21), 7198. https://doi.org/10.3390/en14217198
Sanchez-Iborra, R., & Skarmeta, A. (2022). Securing the Hyperconnected Healthcare Ecosystem. In AI and IoT for Sustainable Development in Emerging Countries. https://doi.org/10.1007/978-3-030-90618-4_22




Comments